In this tutorial, we are going to discuss How To Check SSL Certificate Expiration with Grafana. Security is more important these days so you have to secure various parts with SSL Certificates while setting up the entire monitoring solutions.
In our previous Prometheus setup on Linux also we have created SSL certificates to ensure the interaction between those agents and grafana was protected.
Also Check: MongoDB Monitoring with Grafana & Prometheus
As time passes, it is common to verify SSL certification expiration and secure the visualizing data. Let’s assume that one of the SSL certificate expiration dates is about to expire. Now, we have to check the ways to secure it.
In today’s guide, we are explaining the simple process to monitor SSL certificate expiration dates with Grafana and Prometheus.
Get Ready?
- What You Will Learn?
- Installing Prometheus & Grafana
- Installing the node-cert exporter in Prometheus
- a – Download the node-cert exporter
- b – Install the node-cert exporter as a service
- c – Binding your exporter to Prometheus
- Creating a Grafana dashboard
- a – Import a Grafana dashboard
- b – Write a PromQL query for SSL certificate expiration
- c – Customizing the threshold levels
- Firing alerts when SSL certificates expire
- a – Creating a rules file
- b – Create an AlertManager rules file
- c – Getting AlertManager alerts on Slack
- Alternatives
What You Will Learn?
Those are the concepts that you are going to learn if you follow this tutorial until the end.
- How to setup Prometheus and Grafana easily
- How to install the node-cert exporter to monitor your SSL certificates.
- How to design a Grafana dashboard to visualize SSL certificate expirations.
- How to raise alerts when your SSL certificates are about to expire.
That’s a long program, let’s start working.
Installing Prometheus & Grafana
The complete Prometheus & Grafana installation has already been covered in one of our previous articles.
It explains how to setup your Prometheus monitoring instance, how to secure it using HTTPS, and how to bind it securely to Grafana.
You can skip the reverse proxy steps, but it is highly recommended to setup an NGINX reverse proxy for safety purposes.
When you are done, you are ready to go to step two.
Do Check: Complete MySQL dashboard with Grafana & Prometheus
Installing the node-cert exporter in Prometheus
Now that our Prometheus & Grafana stack is ready, it is time to install the node-cert exporter.
The node-cert exporter is an exporter that will periodically check your SSL certificates given a set of filesystem paths.
It is highly recommended to store your SSL certificates in the /etc/ssl folder, but you may store them in different places.
- Complete Node Exporter Mastery with Prometheus | Monitoring Linux Host Metrics WITH THE NODE EXPORTER
- Complete MySQL dashboard with Grafana & Prometheus | MySQL Database Monitoring using Grafana and Prometheus
- How To Install Prometheus with Docker on Ubuntu 18.04
a – Download the node-cert exporter
To download the node-cert exporter, run a simple wget command.
$ wget https://github.com/amimof/node-cert-exporter/releases/latest/download/node-cert-exporter-linux-amd64
You should now have the node-cert-exporter executable on your instance.
Move this executable to your /usr/local/bin folder and make it executable, at least for the owner of the file.
$ sudo mv node-cert-exporter-linux-amd64 /usr/local/bin $ sudo chmod u+x /usr/local/bin/node-cert-exporter-linux-amd64
Create a user for the node-cert exporter.
$ sudo useradd -rs /bin/false node-cert-exporter
Make the node-cert-exporter user the owner of the exporter executable.
$ sudo chown node-cert-exporter:node-cert-exporter /usr/local/bin/node-cert-exporter-linux-amd64
This should be the content of your bin folder.
![]()
b – Install the node-cert exporter as a service
As always, we are going to install the exporter as a service.
Running exporters as a background process is the best way to crash them. Plus, you can monitor your systemd services and be notified when one goes down.
As always, head to the /lib/systemd/system folder, and create a node-cert service file in there.
$ cd /lib/systemd/system $ sudo touch node-cert-exporter.service
The node-cert exporter uses the path flag to specify where your certificates are located on your system.
In my case, I am going to suppose that my certificates are located in the /etc/ssl/certs folder.
Make sure to finetune the path flag for your own SSL path.
Here is the content of the service file.
[Unit]
Description=Node Cert Exporter
Wants=network-online.target
After=network-online.target
[Service]
Type=simple
User=node-cert-exporter
Group=node-cert-exporter
ExecStart=/usr/local/bin/node-cert-exporter-linux-amd64 \
--path=/etc/ssl/certs
Restart=always
[Install]
WantedBy=multi-user.target
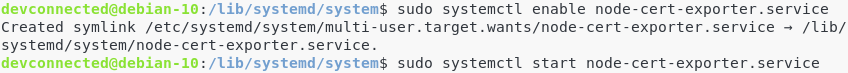
Enable your service, and start it.
$ sudo systemctl enable node-cert-exporter $ sudo systemctl start node-cert-exporter
Great!
Let’s have a look at the metrics exposed by the node-cert exporter.
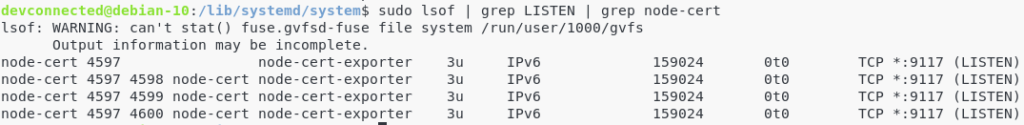
$ sudo lsof | grep LISTEN | grep node-cert
Given the information of the last column, we can see that the node-cert exposes metrics on the port 9117.
Let’s do a quick curl command to see if it is aggregating metrics correctly.
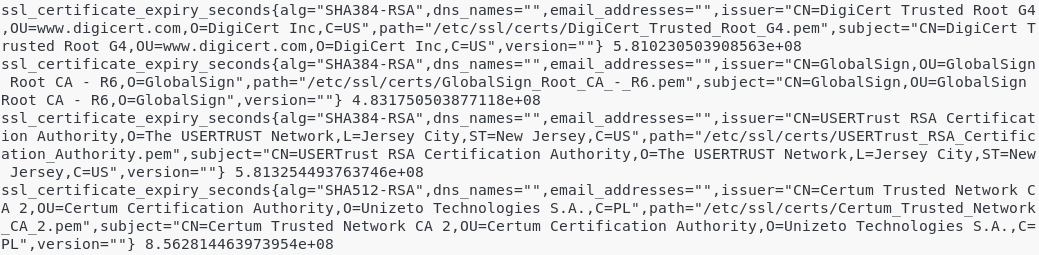
$ curl http://localhost:9117/metrics
If you are seeing metrics named “ssl_certificate_expiry_date“, congratulations!
Your node-cert exporter is correctly installed.
c – Binding your exporter to Prometheus
Now that your node-cert exporter is correctly running, you need to bind it to Prometheus.
To do so, navigate to your Prometheus configuration file, and start editing it to add the following targets.
$ cd /etc/Prometheus $ sudo vi prometheus.yml
In the static_configs part of your configuration file, add a new entry for the cert exporter.
static_configs:
- targets: ['localhost:9090', 'localhost:9117']
Restart Prometheus for your changes to be applied.
$ sudo systemctl restart prometheus
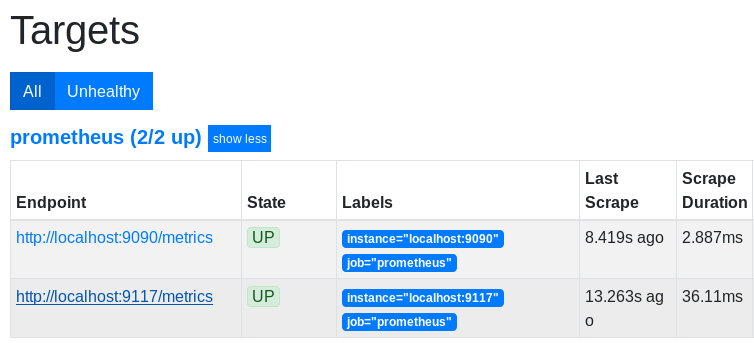
Don’t forget to verify that Prometheus is actively scraping your new target.
Head over to http://localhost:1234/targets (if you followed the Prometheus and Grafana tutorial).
Awesome! The exporter is up and running.
Time to check the SSL certificate expirations in Grafana.
Creating a Grafana dashboard
In order to visualize SSL certification expiration dates, we are going to use a predefined dashboard built by the creator of the exporter.
a – Import a Grafana dashboard
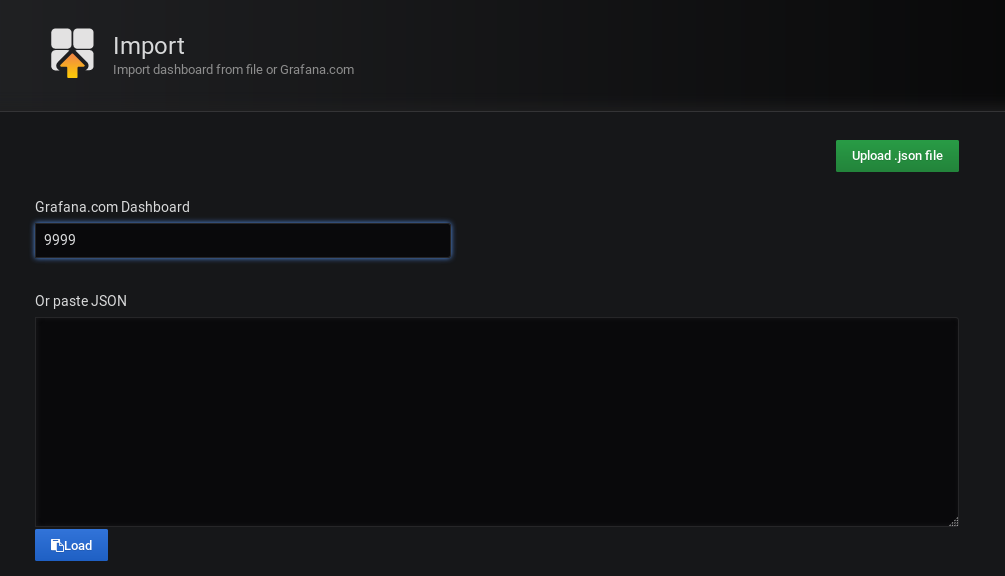
To import a Grafana dashboard, click on the Import option available in the left menu.
In the next window, choose to import your dashboard given a dashboard ID.
The dashboard ID for the node-cert dashboard is 9999.
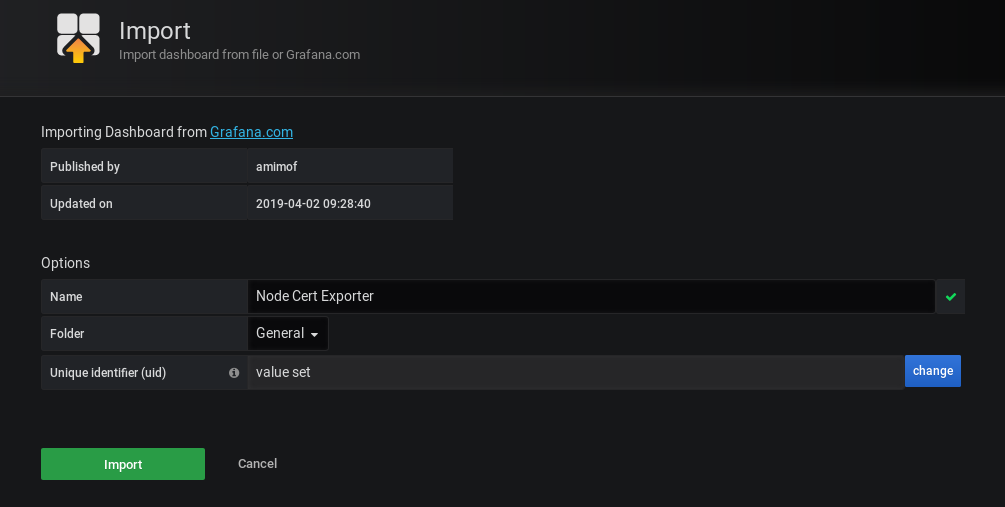
From there, Grafana should automatically detect that you are trying to import the dashboard.
This is what you should see.
b – Write a PromQL query for SSL certificate expiration
By default, the dashboard is not fully loaded in Grafana.
For some reasons that I ignore, the PromQL query is not actively loaded. That’s not a big problem, we are going to write it our way.
Edit the table panel in your dashboard.
Go to the query panel, select Prometheus as a datasource and write the following PromQL query.
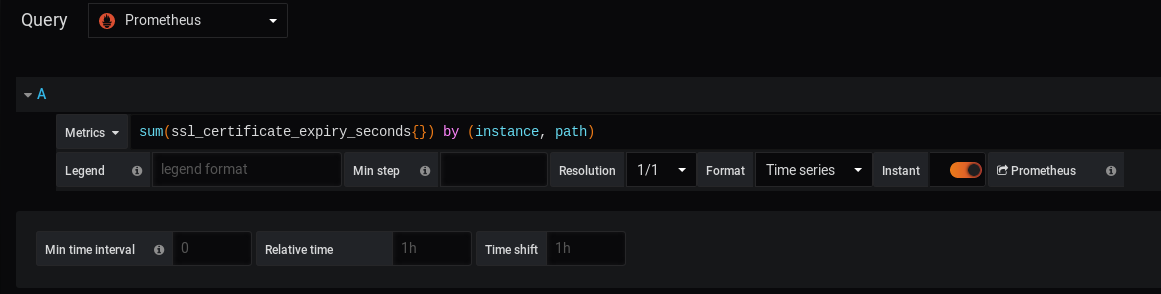
Important Note: Do not forget to check the “Instant” option on the second line of your query panel (otherwise you won’t be able to see anything)
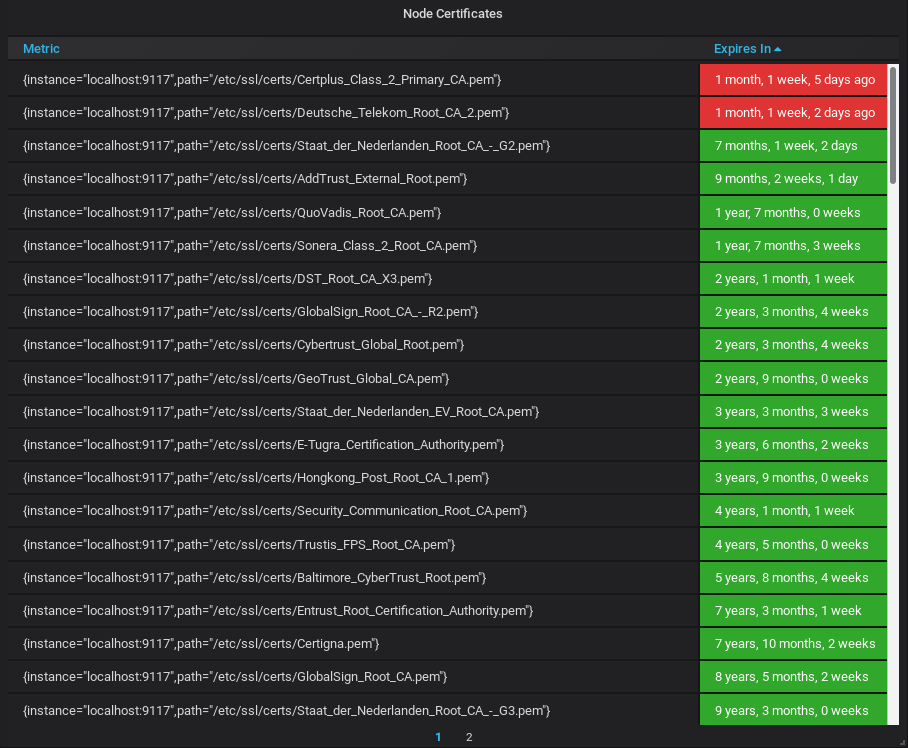
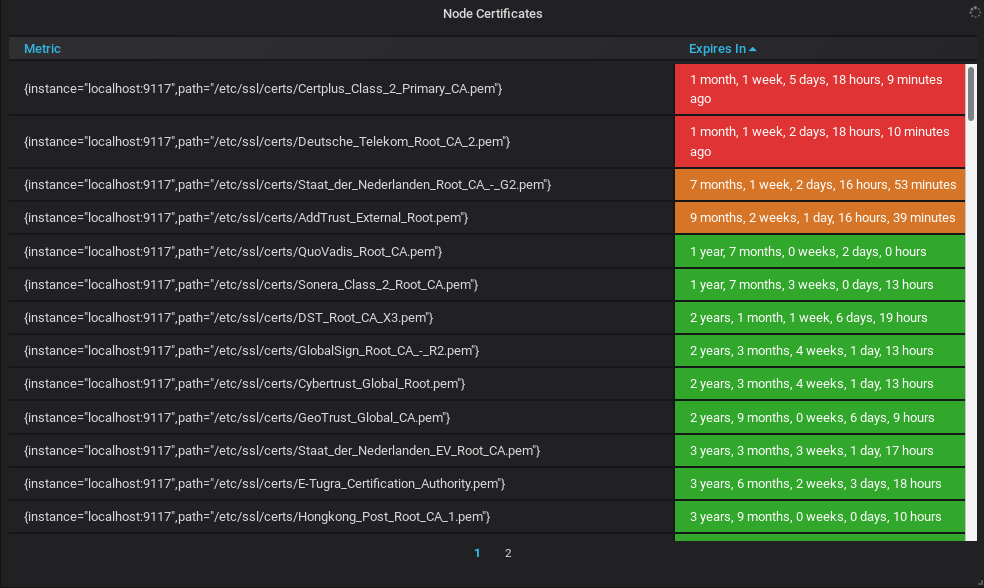
This is what you should now see on your dashboard.
Awesome!
You now have a dashboard checking your SSL certificates with pleasing colors.
As you can see, most of my certificates are safe, but some of them will have to be renewed in a month or so.
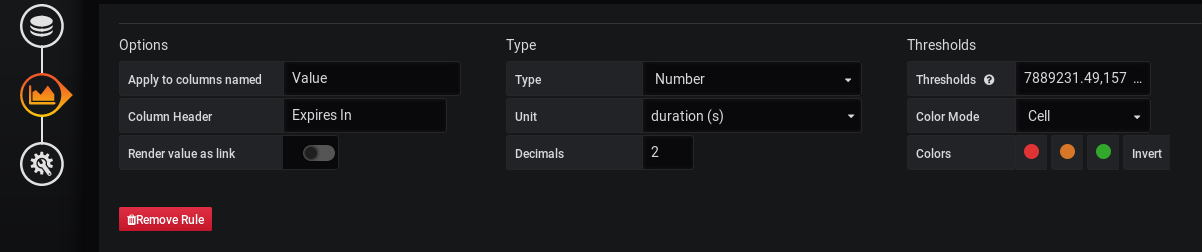
c – Customizing the threshold levels
As you can see, some thresholds are already defined in this Grafana dashboard.
By default, red lines will be displayed for SSL certificates that need to be renewed in less than three months, orange lines between three months and six months, and green lines for more than six months.
Would you like to customize those levels?
Let’s have red lines for expirations in less than one week, and orange between one week and one month.
To customize it, head over to the “Visualization” panel in Grafana and search for the corresponding option line.
The levels are stored in the “Thresholds” text field.
The current values are 7889231 seconds (3 months) and 15778463 seconds (6 months).
Let’s modify this text field for 2592000 (1 month) and 25920000 (10 months).
604800,2592000
Firing alerts when SSL certificates expire
If you are to check your SSL certification expiration dates, it is very likely that you are not going to take a look at your dashboard every day.
You want to be alerted when one of your certificates is about to expire.
Make sure to install the AlertManager with Prometheus by following this tutorial.
a – Creating a rules file
In your Prometheus folder, create a “alerts” folder. This is the place where you are going to store all your alert files.
Go to your alerts folder, and create a new file named “ssl_rules.yml“.
$ cd /etc/prometheus $ sudo mkdir alerts && cd alerts $ sudo nano ssl_rules.yml
In the file, paste the following content.
groups:
- name: ssl_expiry.rules
rules:
- alert: SSLCertExpiringSoon
expr: sum(ssl_certificate_expiry_seconds{}) by (instance, path) < 86400 * 30
for: 10mThe following configuration will fire an alert when you need to check your SSL certificate (one month away from being expired)
As a reminder, the Prometheus server is going to be used as a client for the Alert Manager.
b – Create an AlertManager rules file
Now we are going to create a rules file for the AlertManager.
For this part, we are going to use Slack as a recipient, but you could send an email, or use PagerDuty for example.
If you are looking to create a Webhook for Slack and Prometheus, check our other articles or go for a web search.
Go to your /etc/alertmanager folder and create a new file named “alertmanager.yml“.
$ cd /etc/alertmanager $ sudo touch alertmanager.yml
Paste the following content in your file (change the webhook URL for the one provided by your Slack workspace)
global:
resolve_timeout: 5m
route:
group_by: ['SSLCertExpiringSoon']
group_wait: 10s
group_interval: 10s
repeat_interval: 1h
receiver: slack
receivers:
- name: slack
slack_configs:
- api_url: $WEBHOOK_URL
channel: '#devconnecteds-blog'
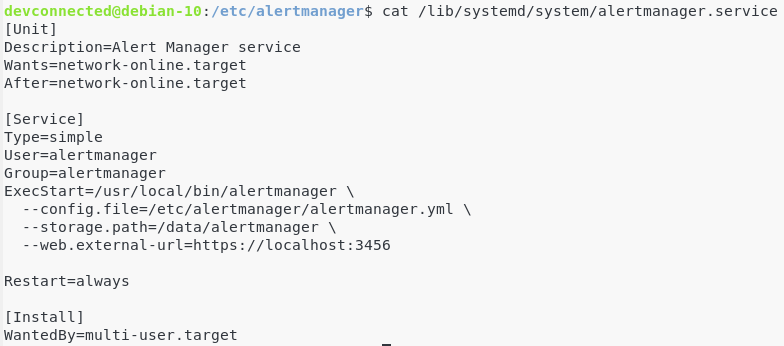
Save your file, and make sure that your AlertManager service is launched with the correct option (with the correct –config flag)
Restart your AlertManager service.
$ sudo systemctl restart alertmanager
c – Getting AlertManager alerts on Slack
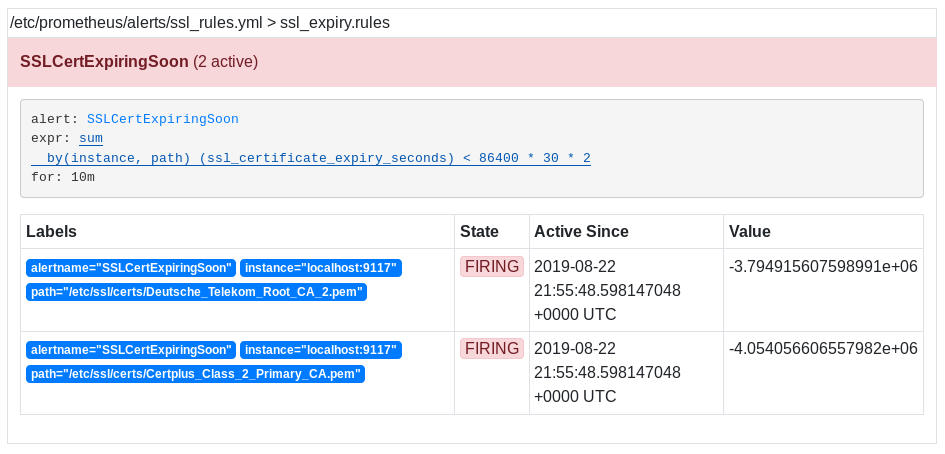
Now that our configuration is set, it is time to have an alert firing on the Prometheus server.
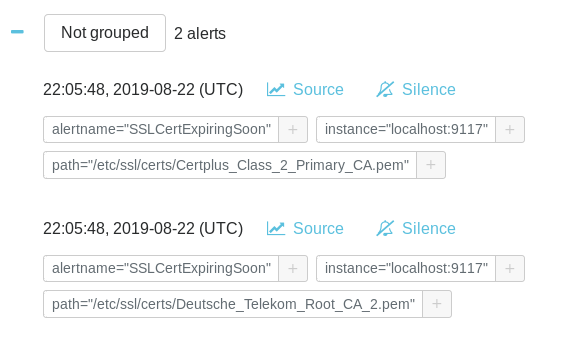
As you can see, two alerts are already firing on my Prometheus alerts tab.
On the AlertManager, this is what you should see.
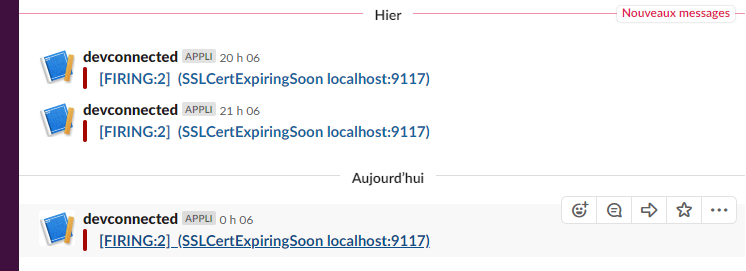
Finally, you should receive your alerts on Slack. In this case, they are grouped, but you can modify this option in your rules file (by replacing the group by option).
Awesome! You are now notified when you have to check your SSL certificates.
Alternatives
Alternatives to Prometheus and Grafana exist to check your SSL certificate expiration.
David McKay, the developer advocate for InfluxData, wrote an article on how to check your SSL certificates using Telegraf and InfluxDB.
This is more or less the same principle, except that you would have to use an InfluxDB datasource in Grafana.
If you are not sure about how to setup the TIG stack, here is how to setup InfluxDB and Grafana on Linux.
Free services also exist if you are looking to monitor your SSL certificates online. Certificate Expiry Monitor is one of them as an example. Are you going to start using Prometheus to monitor your SSL certificates?
I hope that you learned something new today. Till next practice well with our useful tutorials on modern technologies.